https://www.nirsoft.net/utils/browsing_history_view.html
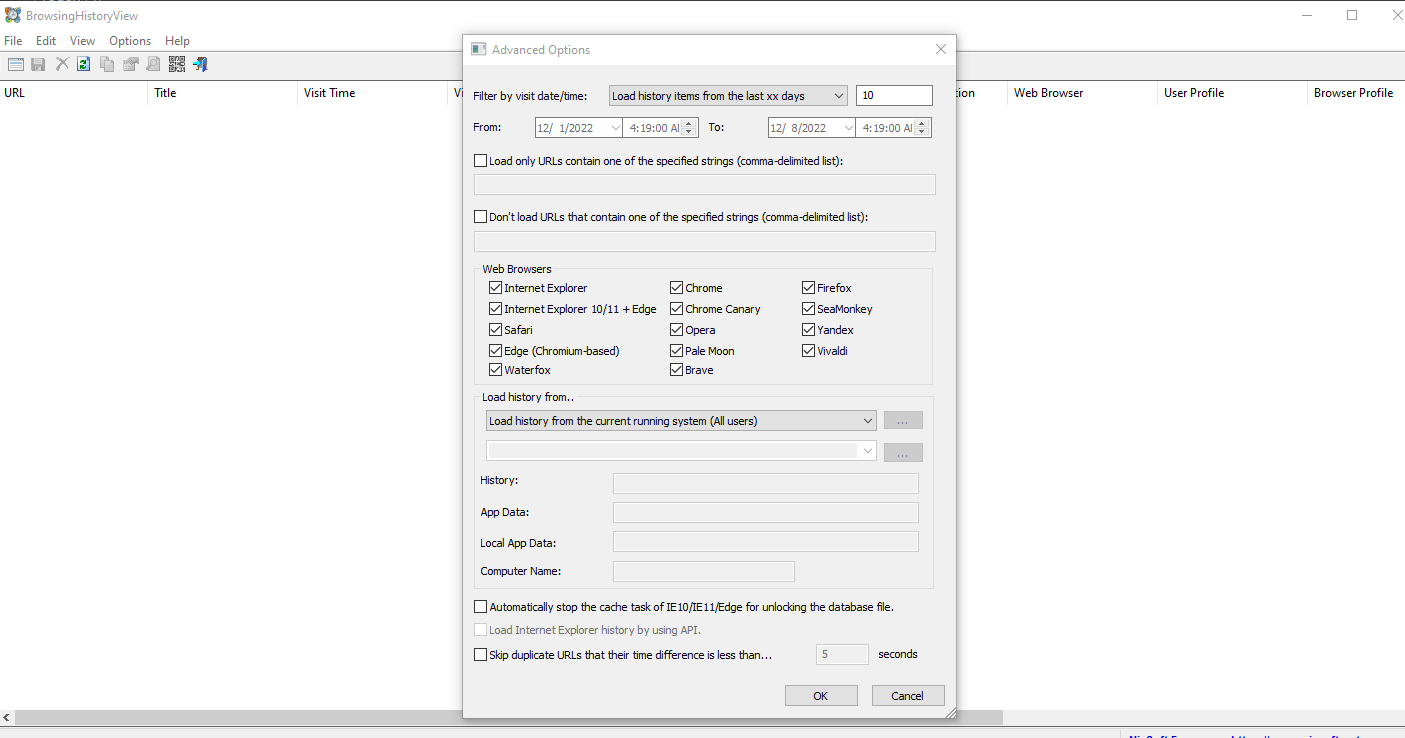
When we install and open the tool we see an advanced options menu where we can apply filters according to our needs, select browsers we want to target etc.

We can filter the web history by its age; by the date and time that the URL visited exactly. You can see that we are setting the filter to display data since the last 10 hours in the below example.
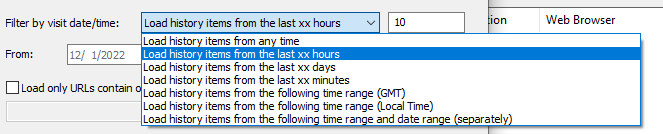
We can also specify the time range and the data to be displayed during the specified timeline. This feature is particularly useful as a Forensic Analyst or Incident Responder because if we know the time frame of when an incident occurs, we can apply date filters around those time frames to pinpoint the user activities before or after the incident. This can help us find the cause of incident or objectives of the attacker (in case of insider threats).

Next, we have 2 types of string based filters:
Matching Strings filter allows us to specify known strings which we want to know if they exist in browser history or not. This can be useful if we have some known IOCs or domain names (Threat actor using multiple randomized subdomains) or we want to know if the user searched for anything specific or not. We can specify multiple strings separated by a comma “,”.
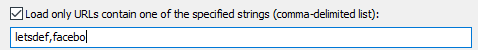
Below example will display the URLs which have “letsdef” and “facebo” in the URL address. As you might have guessed, the below filter will display all URLs which belong to letsdefend and/or facebook or have these specified strings in URL (which is not likely).
Non-Matching Strings filter allows us to specify known strings which we don't want to be displayed. This can be useful if we want to cut down the noise and filter out known good URLs (Maybe common in organizations like company web portals etc.). We can specify multiple strings separated by a comma “,”.
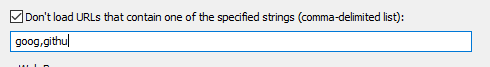
Below example will not display URLs which have “goog” and "githu" string in URL address. We can guess that this filter will not display any google or github domains.
We can use both these match/non-match filters concurrently which will make our analysis easier if we have large amount of data.
Next, we can select browsers from which to collect data;
We can also select the user/profile to be analyzed on the system. This can be very helpful in Active Directory environments or where multiple users are sharing a workstation.